* feat: Configurable Unique Machine Identification This change fixes Segfault on AWS App Runner with v2 #3625 The change introduces two new dependencies: * github.com/drone/envsubst for supporting AWS ECS, which has its metadata endpoint described by an environment variable * github.com/jarcoal/jpath so that only relevant data from a metadata response is used to identify the machine. The change ads new configuration (see `defaults.yaml`): * `Machine.Identification` enables configuration of how machines are uniquely identified - I'm not sure about the top level category `Machine`, as I don't have anything else to add to it. Happy to hear suggestions for better naming or structure here. * `Machine.Identifiation.PrivateId` turns on or off the existing private IP based identification. Default is on. * `Machine.Identification.Hostname` turns on or off using the OS hostname to identify the machine. Great for most cloud environments, where this tends to be set to something that identifies the machine uniquely. Enabled by default. * `Machine.Identification.Webhook` configures identification based on the response to an HTTP GET request. Request headers can be configured, a JSONPath can be set for processing the response (no JSON parsing is done if this is not set), and the URL is allowed to contain environment variables in the format `"${var}"`. The new flow for getting a unique machine id is: 1. PrivateIP (if enabled) 2. Hostname (if enabled) 3. Webhook (if enabled, to configured URL) 4. Give up and error out. It's important that init configures machine identity first. Otherwise we could try to get an ID before configuring it. To prevent this from causing difficult to debug issues, where for example the default configuration was used, I've ensured that the application will generate an error if the module hasn't been configured and you try to get an ID. Misc changes: * Spelling and gramatical corrections to `init.go::New()` long description. * Spelling corrections to `verify_zitadel.go::newZitadel()`. * Updated `production.md` and `development.md` based on the new build process. I think the run instructions are also out of date, but I'll leave that for someone else. * `id.SonyFlakeGenerator` is now a function, which sets `id.sonyFlakeGenerator`, this allows us to defer initialization until configuration has been read. * Update internal/id/config.go Co-authored-by: Alexei-Barnes <82444470+Alexei-Barnes@users.noreply.github.com> * Fix authored by @livio-a for tests Co-authored-by: Livio Amstutz <livio.a@gmail.com> |
||
|---|---|---|
| .codecov | ||
| .github | ||
| build | ||
| cmd | ||
| console | ||
| deploy/compose | ||
| docs | ||
| guides | ||
| internal | ||
| openapi | ||
| pkg/grpc | ||
| proto/zitadel | ||
| statik | ||
| tools | ||
| .dockerignore | ||
| .gitignore | ||
| .goreleaser.yaml | ||
| .releaserc.js | ||
| changelog.config.js | ||
| CODE_OF_CONDUCT.md | ||
| CONTRIBUTING.md | ||
| go.mod | ||
| go.sum | ||
| LICENSE | ||
| main.go | ||
| README.md | ||
| SECURITY.md | ||
You want auth that's quickly set up like Auth0 but open source like Keycloak? Look no further— ZITADEL combines the ease of Auth0 and the versatility of Keycloak.
We provide a wide range of out of the box features like secure login, self-service, OpenID Connect, OAuth2.x, SAML2, branding, Passwordless with FIDO2, OTP, U2F, and an unlimited audit trail to improve the life of developers. Especially noteworthy is that ZITADEL supports not only B2C and B2E scenarios but also B2B. This is super useful for people who build B2B Solutions, as ZITADEL can handle all the delegated user and access management.
With ZITADEL you rely on a battle tested, hardened and extensible turnkey solution to solve all of your authentication and authorization needs. With the unique way of how ZITADEL stores data it gives you an unlimited audit trail which provides a peace of mind for even the harshest audit and analytics requirements.
🏡 Website 💬 Chat 📋 Docs 🧑💻 Blog 📞 Contact
Get started
ZITADEL Cloud
The easiest way to get started with ZITADEL is to use our public cloud offering. Subscribe to our newsletter and we will be in touch with you as soon as the public release is live.
You can also discovery our new pay-as-you-go pricing.
Install ZITADEL
Quickstarts - Integrate your app
- Multiple Quickstarts can be found here
- And even more examples are located under zitadel/zitadel-examples
If you miss something please feel free to engage with us here
Why ZITADEL
- API-first
- Strong audit trail thanks to event sourcing
- Actions to react on events with custom code
- Branding for a uniform user experience
- CockroachDB is the only dependency
Features
- Single Sign On (SSO)
- Passwordless with FIDO2 support
- Username / Password
- Multifactor authentication with OTP, U2F
- Identity Brokering
- Machine-to-machine (JWT profile)
- Personal Access Tokens (PAT)
- Role Based Access Control (RBAC)
- Delegate role management to third-parties
- Self-registration including verification
- User self service
- Service Accounts
- OpenID Connect certified
- 🚧 SAML 2.0
Client libraries
| Language | Client | API | Machine auth (*) | Auth check (**) | Thanks to the maintainers |
|---|---|---|---|---|---|
| .NET | zitadel-net | GRPC | ✔️ | ✔️ | buehler 👑 |
| Dart | zitadel-dart | GRPC | ✔️ | ❌ | buehler 👑 |
| Elixir | zitadel_api | GRPC | ✔️ | ✔️ | jshmrtn 🙏🏻 |
| Go | zitadel-go | GRPC | ✔️ | ✔️ | ZITADEL |
| Rust | zitadel-rust | GRPC | ✔️ | ❌ | buehler 👑 |
| JVM | 🚧 WIP | ❓ | ❓ | TBD | |
| Python | 🚧 WIP | ❓ | ❓ | TBD | |
| Javascript | ❓ | ❓ | ❓ | Maybe you? |
(*) Automatically authenticate service accounts with JWT Profile.
(**) Automatically check if the access token is valid and claims match
How To Contribute
Details about how to contribute you can find in the Contribution Guide
Contributors
Made with contrib.rocks.
Showcase
Passwordless Login
Use our login widget to allow easy and secure access to your applications and enjoy all the benefits of passwordless (FIDO 2 / WebAuthN):
- works on all modern platforms, devices, and browsers
- phishing resistant alternative
- requires only one gesture by the user
- easy enrollment of the device during registration
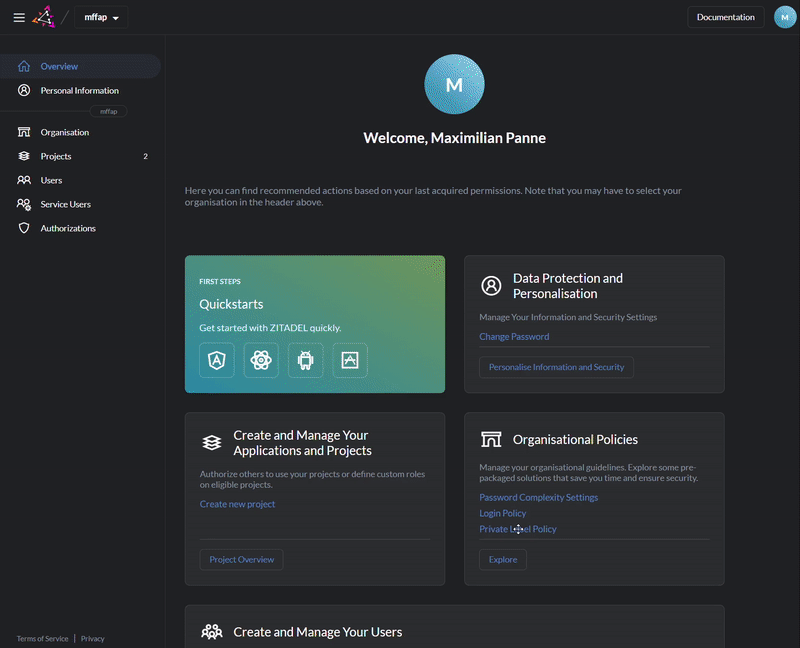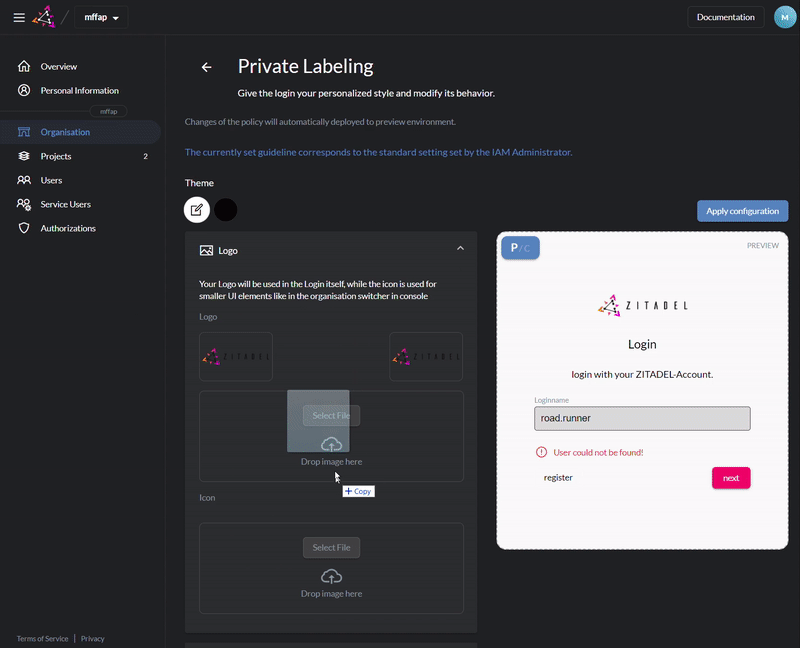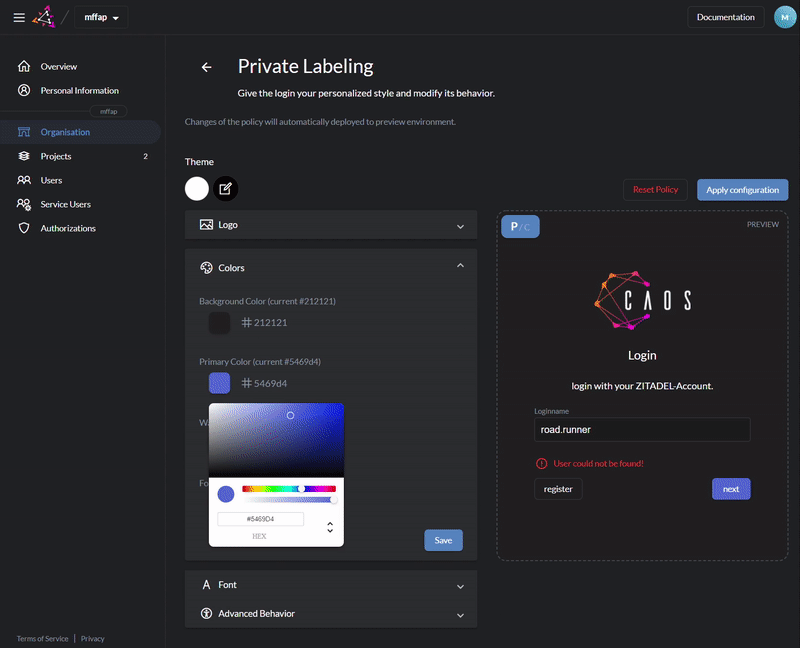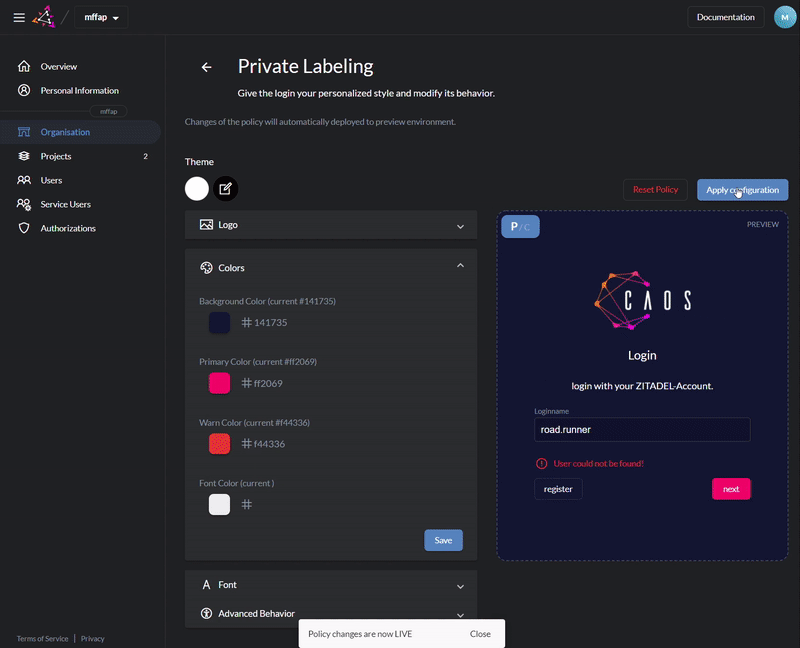
Admin Console
Use Console or our APIs to setup organizations, projects and applications.
Delegate the right to assign roles to another organization

Customize login and console with your design
Usage Data
ZITADEL components send errors and usage data to CAOS Ltd., so that we are able to identify code improvement potential. If you don't want to send this data or don't have an internet connection, pass the global flag --disable-analytics when using zitadelctl. For disabling ingestion for already-running components, execute the takeoff command again with the `` flag.
We try to distinguishing the environments from which events come from. As environment identifier, we enrich the events by the domain you have configured in zitadel.yml, as soon as it's available. When it's not available and you passed the --gitops flag, we defer the environment identifier from your git repository URL.
Besides from errors that don't clearly come from misconfiguration or cli misusage, we send an initial event when any binary is started. This is a " invoked" event along with the flags that are passed to it, except secret values of course.
We only ingest operational data. Your ZITADEL workload data from the IAM application itself is never sent anywhere unless you chose to integrate other systems yourself.
Security
See the policy here
License
See the exact licensing terms here
Unless required by applicable law or agreed to in writing, software distributed under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. See the License for the specific language governing permissions and limitations under the License.